Securing Voyage Data Recorder (VDR) Connectivity for IEC 61162-460 Aligned Bridge Networks
A Robustel Application Example
Application Example – Fast Facts
Industry
Maritime (commercial vessels)
Product(s)
MG460 gateway with MG Core; RCMS (RobustLink, RobustVPN); optional Edge data handling where appropriate
Challenges
Protect VDR interfaces and bridge networks, maintain clean segmentation, enable controlled vendor access, and prepare for audits
Expected Outcomes
IEC 61162-460–aligned network design, reliable data paths to VDR and navigation systems, auditable change control, and faster inspections
From “just connected” to “provably secure” on the bridge
A Voyage Data Recorder (VDR) is mandatory under International Maritime Organization (IMO) SOLAS and is central to incident investigation and compliance. Yet VDRs often sit on bridge networks that have grown organically mixing Electronic Chart Display and Information System (ECDIS), radar, Automatic Identification System (AIS), GNSS/NMEA sources, maintenance laptops, and occasional vendor access. Operators need a vessel gateway pattern that keeps the VDR reachable, the bridge network segmented and controlled, and the whole design aligned with IEC 61162-460 and the cyber objectives of International Association of Classification Societies (IACS) Unified Requirements UR E26 and UR E27
Business Challenges
Network segregation on the bridge: Separate navigation/OT traffic from maintenance and crew access while keeping essential data flowing to the VDR.
Access control and accountability: Allow vendor/service access for ECDIS, radar, or VDR maintenance, but only with least privilege, time limits, and a full audit trail.
Change management: Ensure configuration, firmware, and policy changes are signed, logged, and reversible—so audits start with evidence, not reconstruction.
Mixed equipment and interfaces: Different vendors, versions, and media (Ethernet, serial gateways, NMEA) require a gateway that enforces policy without forcing wholesale hardware replacement.
Inspection readiness: Provide clear artifacts—topology, segmentation rules, accounts/roles, and change history—that support IEC 61162-460 aligned designs and IACS UR E26/E27 cyber requirements.
Solution Overview
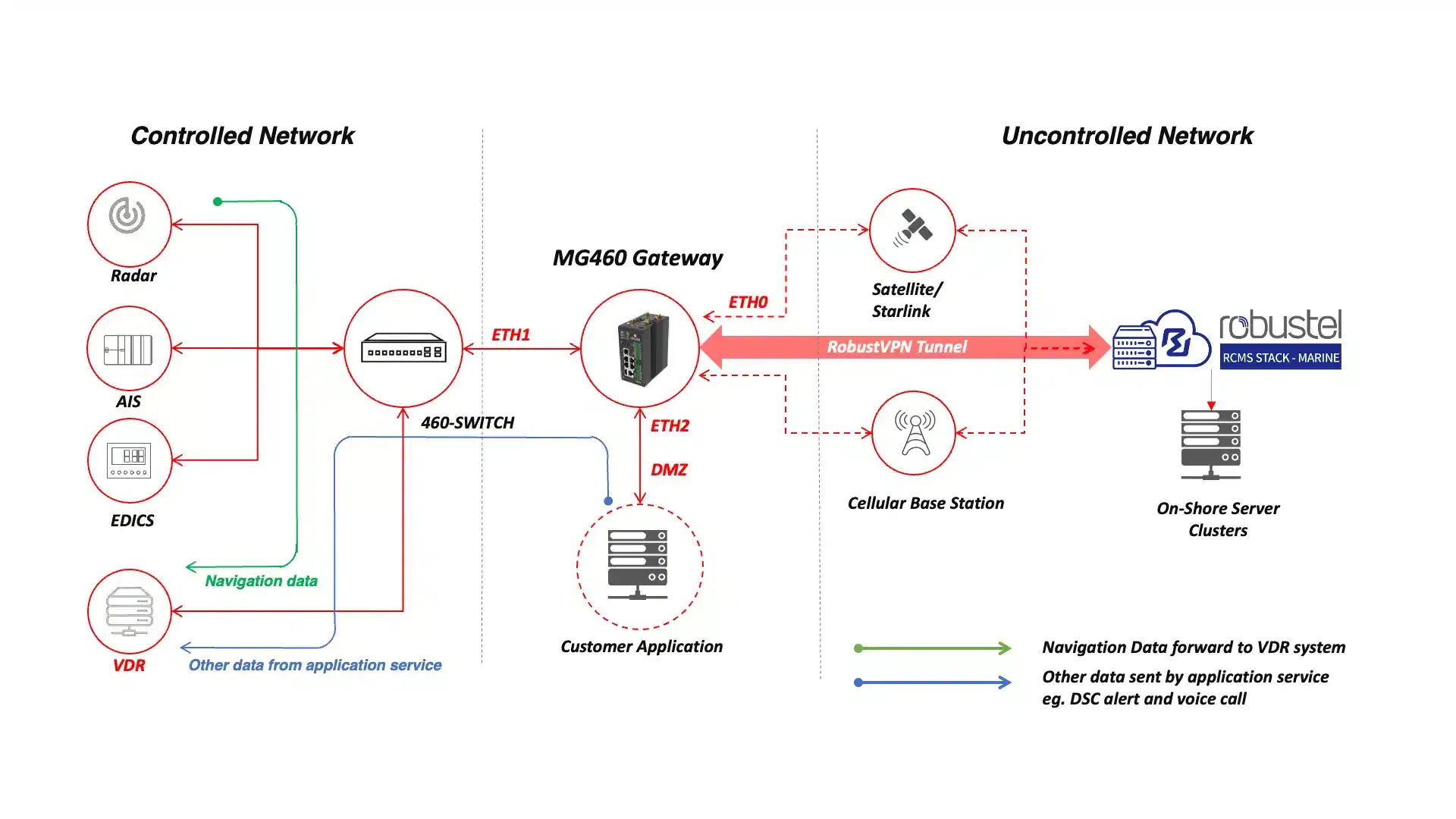
Here’s how we turn the bridge into a controlled, auditable environment—without breaking operations. We start with a compliant gateway foundation (MG460 with MG Core), establish IEC 61162-460–aligned segmentation and access rules, and add the minimum services needed for vendor access and fleet operations. The result is a standardized pattern you can roll across vessels and present confidently during audits.
- Compliant gateway foundation: Deploy MG Core on MG460 Gateway to enforce segmentation, least-privilege access, services-off-by-default, signed updates, and clear logging—supporting IACS UR E26/E27 cyber objectives and IEC 61162-460 network design principles.
- Bridge/OT segmentation: Use VLANs and firewall policy to separate Navigation/VDR, Maintenance/Vendor, and Crew/Guest zones; define permitted flows (e.g., NTP to time sources, VDR ingest from approved talkers, no lateral movement from maintenance/guest).
- Controlled vendor access: Provide RobustVPN profiles bound to roles and devices, with time-boxed credentials and per-service exposure (e.g., only ECDIS SSH/HTTPS during a maintenance window). Activity is logged for audit.
- Fleet operations at scale: With RCMS, standardize templates per vessel class, onboard via Zero-Touch, roll out firmware/policy in rings, and maintain a complete configuration and event history across ships.
Note: VDR, ECDIS, radar and sensor integrations follow the equipment list and class-approved plan. The gateway does not alter certified instrumentation; it protects, segments, and monitors the network around it.
Expected Customer Outcomes
You achieve a IEC 61162-460–aligned bridge network with clear segmentation around the VDR; vendor access is least-privilege and time-limited with full audit trails; and configuration, firmware, and policy changes are signed, versioned, and reversible. The result is reliable VDR data paths, lower support effort, and smoother IACS UR E26/E27 and inspection discussions across the fleet.
Featured Products
Robustel MG460 Gateway

MG Core Operating System

RCMS Cloud Device Management

Talk to an Expert
Every bridge is different. Share your VDR and navigation stack, current topology, and class expectations we’ll design a gateway pattern that protects the VDR, aligns with IEC 61162-460, and scales across your vessels.
