Protecting ECDIS Connectivity with IEC 61162-460 Aligned Segmentation
A Robustel Application Example
Application Example – Fast Facts
Industry
Maritime (commercial vessels)
Product(s)
MG460 gateway with MG Core; RCMS (RobustLink, RobustVPN); optional Edge data handling where appropriate
Challenges
Keep Electronic Chart Display and Information System (ECDIS) reachable without exposing the bridge network; enforce least-privilege vendor access; maintain signed, auditable changes; prepare clean evidence for International Association of Classification Societies (IACS) Unified Requirements UR E26 and UR E27 and IEC 61162-460 assessments
Expected Outcomes
IEC 61162-460–aligned segmentation on the bridge, predictable ECDIS data paths, controlled remote access, faster and smoother inspections
Keep ECDIS online without opening the bridge
ECDIS sits at the heart of navigation alongside radar, Automatic Identification System (AIS), GNSS/NMEA talkers, VDR, and maintenance laptops. Many bridges evolved from flat networks and ad-hoc access paths. Operators need a standard gateway pattern that preserves essential ECDIS services (chart updates, time sync, approved talker/listener flows) while enforcing segmentation and producing the evidence auditors expect for IACS UR E26/E27 and IEC 61162-460.
Business Challenges
Segregation without disruption: Permit only required ECDIS flows (e.g., NTP, chart updates, approved talkers/listeners) and block lateral movement.
Vendor access with accountability: Allow OEM/service access only with role binding, time limits, and a complete activity trail.
Change control: Keep firmware, policy, and configuration signed, logged, and reversible so audits start with evidence, not recollection.
Mixed vendors, mixed media: Ethernet and serial gateways, different ECDIS versions, and legacy devices demand policy enforcement without wholesale replacement.
Inspection readiness: Provide topology, segmentation rules, accounts/roles, and change history aligned to IEC 61162-460 and IACS UR E26/E27 cyber objectives.
Solution Overview
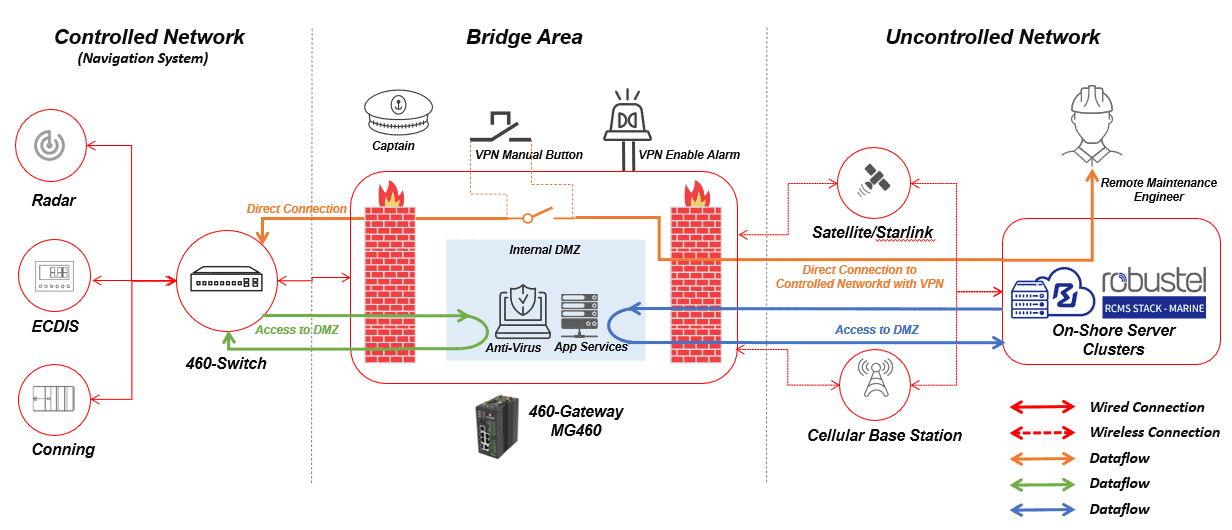
Here’s how we bring ECDIS into a controlled, auditable design—without adding operational friction. We start with a compliant gateway foundation (MG460 with MG Core), implement IEC 61162-460–aligned zones and policy, and add only what’s needed for vendor access and fleet operations. The result is a repeatable pattern you can deploy across vessel classes and present confidently to class.
- Compliant gateway foundation: Run MG Core on MG460 to enforce segmentation, least-privilege access, services-off-by-default, signed updates, and comprehensive logging—supporting IACS UR E26/E27 and IEC 61162-460 aligned designs.
- Bridge/OT segmentation for ECDIS: Use VLANs and firewall rules to separate Navigation/ECDIS, Maintenance/Vendor, and Crew/Guest zones; explicitly permit required flows and deny lateral movement.
- Controlled vendor access: Provide RobustVPN profiles bound to roles and devices, with time-boxed credentials and per-service exposure (e.g., enabling only ECDIS HTTPS/SSH during a maintenance window). Activity is logged for audit.
- Fleet operations at scale: With RCMS, standardize templates per vessel class, commission via Zero-Touch, execute ring-based firmware/policy rollouts, and maintain configuration and event history across ships.
Note: ECDIS integrations follow your equipment list and class-approved plan. The gateway does not alter certified instrumentation; it protects, segments, and monitors the network around it.
Expected Customer Outcomes
Here’s what a successful implementation looks like outcomes that matter to bridge teams, IT, and class.
- Inspection-ready evidence: Topology, rules, accounts, and change history available on request—smoother IACS UR E26/E27 discussions and faster audits.
- IEC 61162-460–aligned segmentation: Clear zones around ECDIS with only approved flows allowed.
- Predictable ECDIS availability: Required services (chart updates, time sync, talker/listener traffic) remain reachable without exposing the wider bridge network.
- Controlled, auditable access: Least-privilege, time-limited vendor access with full activity trails.
- Signed, reversible change control: Firmware, policy, and configuration changes are versioned and verifiable.
Featured Products
Robustel MG460 Gateway

MG Core Operating System

RCMS Cloud Device Management

Talk to an Expert
Every bridge stack is different. Share your ECDIS model, navigation layout, and class expectations—we’ll design a gateway pattern that protects ECDIS, aligns with IEC 61162-460, and scales across your vessels.
